Most drivers consider the smart key system one of the safest and most convenient features in modern cars. Within that system, the key fob is the handheld transmitter that acts as a digital key, allowing the vehicle to recognize its owner and grant access. The convenience feels effortless because it is built on a layered RF authentication process in which the key fob and the vehicle’s central controller continuously exchange and verify data before any door unlocks or the engine starts.
As manual actions shrink, exposure grows. The fewer physical steps a driver performs, the easier it becomes for attackers to interfere with the vehicle’s digital authentication. Real incidents across markets have documented relay attacks, replay attacks, and weaknesses in rolling code implementations. When the unlock, start, or remote-control sequence becomes a poorly protected digital handshake, it turns into a target. In a software-defined vehicle era, the key fob is a tempting entry point.
Studies have shown that low-cost signal amplifiers or customized RF tools can trick the car into “believing” the key is nearby, which enables unlocking or engine start without breaking cryptography at all (see Francillon et al., USENIX Security 2011).
In this context, security testing becomes a critical line of defense for modern vehicles. It is not limited to head units or complex ECUs. Well-designed programs also simulate real attack paths against small components like key fobs, RF modules, or the BCM, so weaknesses can be exposed and fixed before they are exploited.
In the larger cybersecurity picture, the key fob looks small but is often the first door an attacker tries to open.
What is a key fob and how does it work
In modern vehicles, a key fob is a compact device that lets users lock or unlock the car and start the engine without a traditional mechanical key. At its core, the fob transmits and receives RF signals to authenticate the user, then passes commands to central controllers such as the ECU or the BCM.
Two operating modes
Modern key fobs usually rely on two communication modes:
- Remote Keyless Entry (RKE) for button-based remote control
- Passive Keyless Entry (PKE) for proximity-based, hands-free access
Both target safe and convenient entry, yet their signaling, authentication flow, and responses differ in important ways.
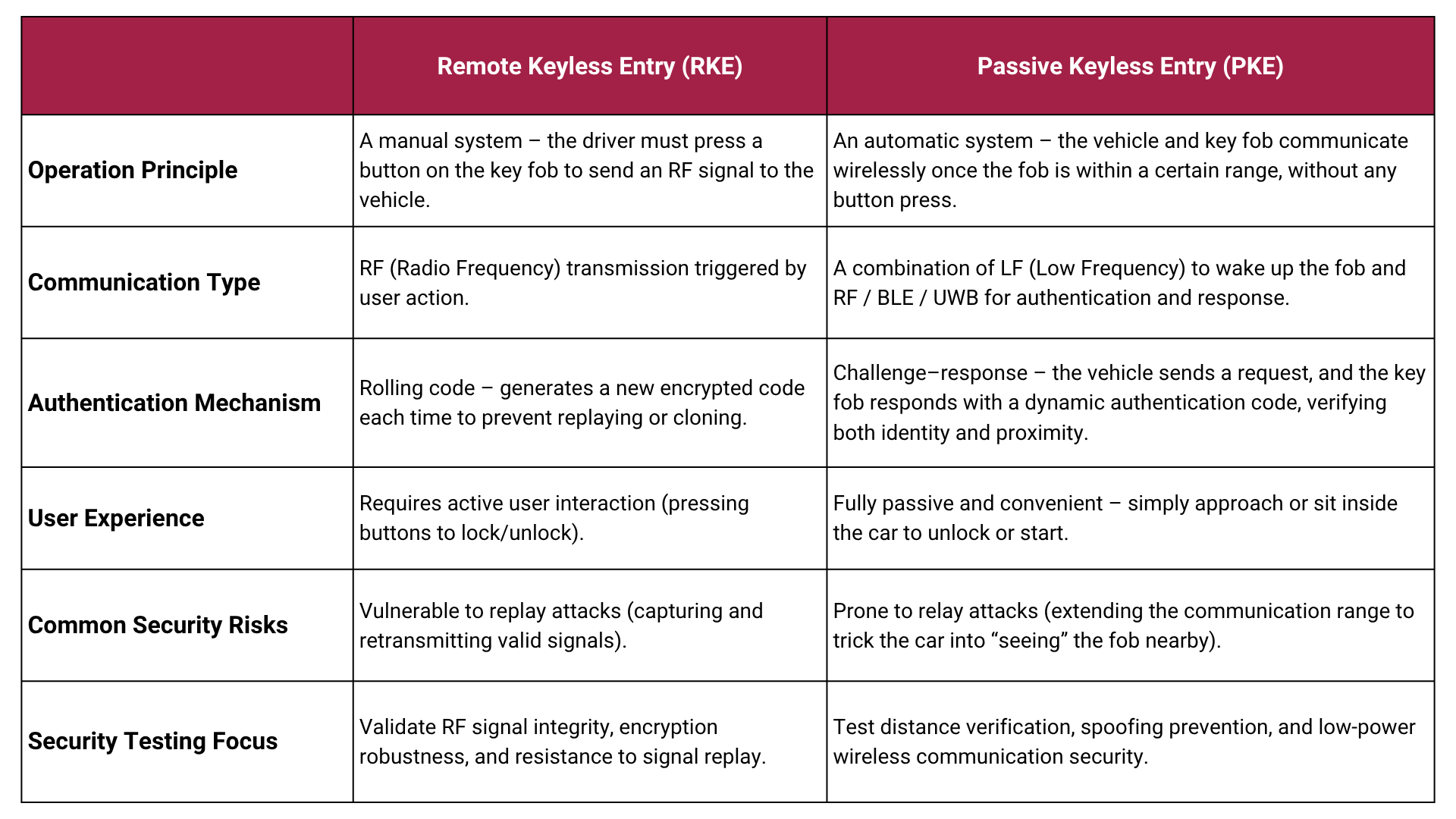
Comparing two key fob mechanisms: RKE vs. PKE
The fob’s role in vehicle authentication and control
User authentication
The key fob proves that the person near the vehicle is authorized. The car verifies this before honoring any command.
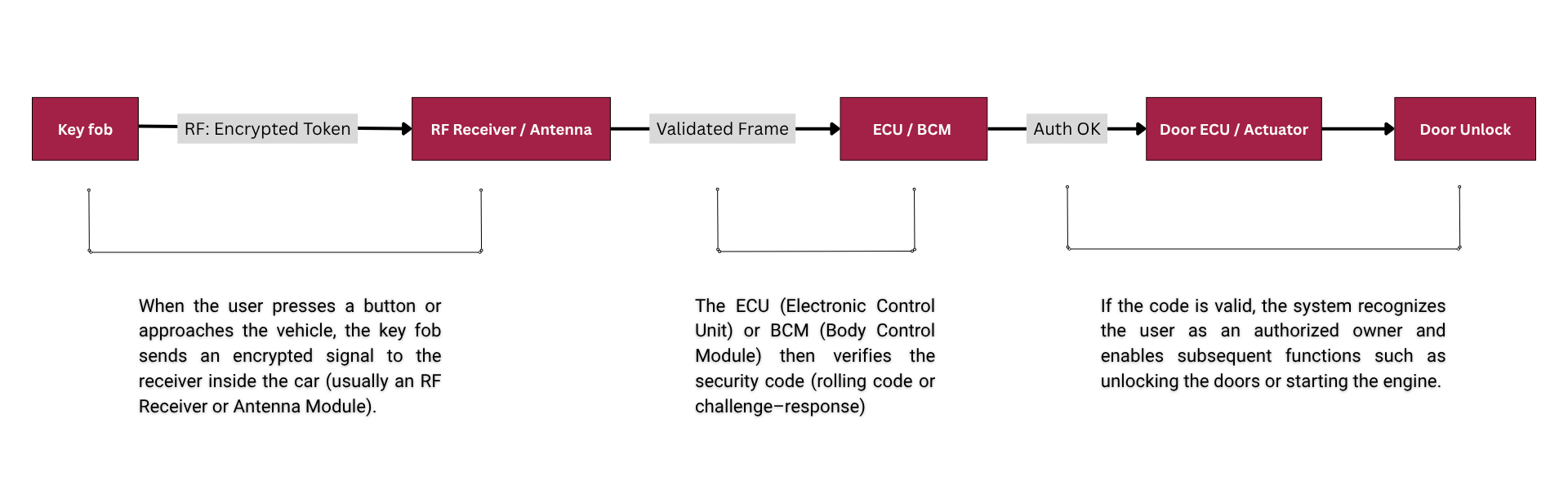
User authentication flow diagram
Engine start authorization
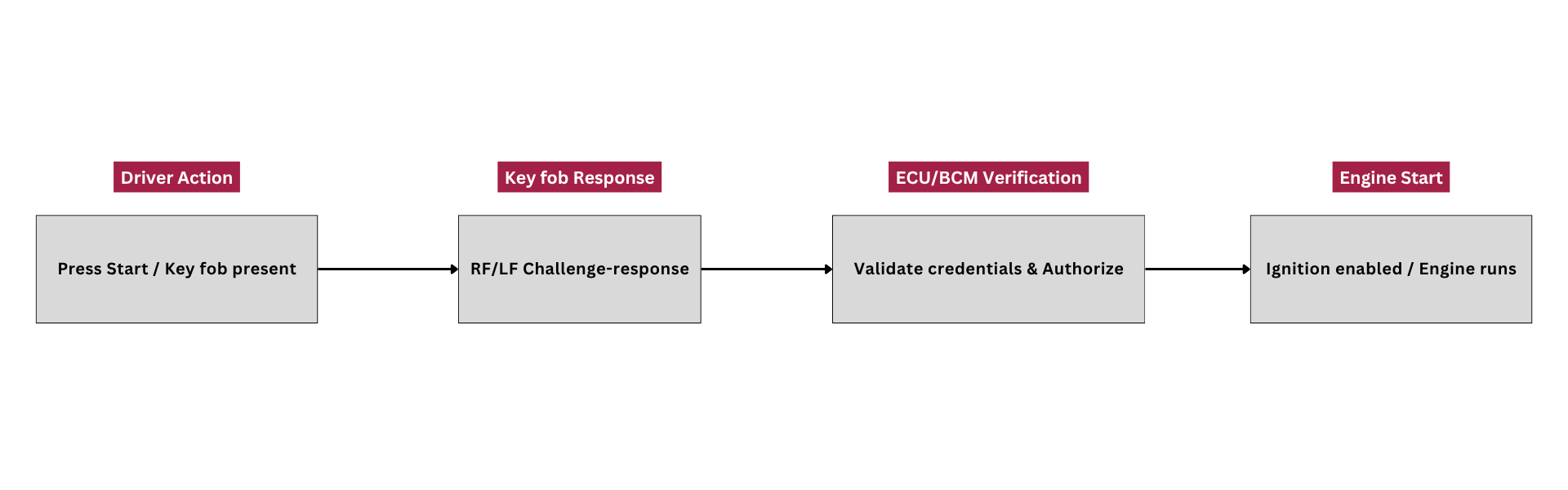
Engine start authorization 4 steps
- When the driver presses Start, the ECU requests an additional check with the fob over a dedicated channel, often RF or LF.
- If the code matches, the ECU enables ignition and the engine starts.
- If it does not, the start sequence is blocked. This is a key safeguard against unauthorized use.
Integration with ECU and BCM
The BCM serves as a hub. It receives the fob’s signal and routes commands to ECUs that handle doors, lighting, alarms, or security. Higher-end models support two-way communication so the fob can display door status or battery level.
The key fob’s promise of effortless, “smart” access also introduces practical security exposure. Design choices such as one-way RF signaling, reliance on rolling-code synchronization, and distance-based trust can open cracks that determine attackers’ probes. In practice, a system that accepts a command without a robust freshness check or message authentication is vulnerable to capture, replay, or subtle timing abuse, even if the cryptography itself is sound.
A modern fob spans several radio links, each with a different risk profile. Low-frequency bands confirm near-field presence for passive entry but can be relayed or spoofed if proximity is trusted too blindly. UHF and ISM channels carry remote commands and are attractive targets for jamming, recording, and later retransmission. Bluetooth Low Energy brings convenience for status feedback and mobile pairing, yet expands the attack surface through additional pairing flows, advertising beacons, and firmware update paths. Taken together, these interfaces deliver convenience, but they also require layered protections such as rolling codes with tight resynchronization windows, strong message authentication, careful power and range management, and continuous security testing to keep real-world threats in check.
Common attacks against key fobs
Replay attack
An attacker records a valid RF message from the fob, such as an unlock command, then replays it later. If the system cannot distinguish new from old messages, the vehicle may unlock or trigger functions without the owner present. Replay is attractive because it does not require breaking encryption or exploiting software. It only requires capturing, storing, and retransmitting valid traffic.
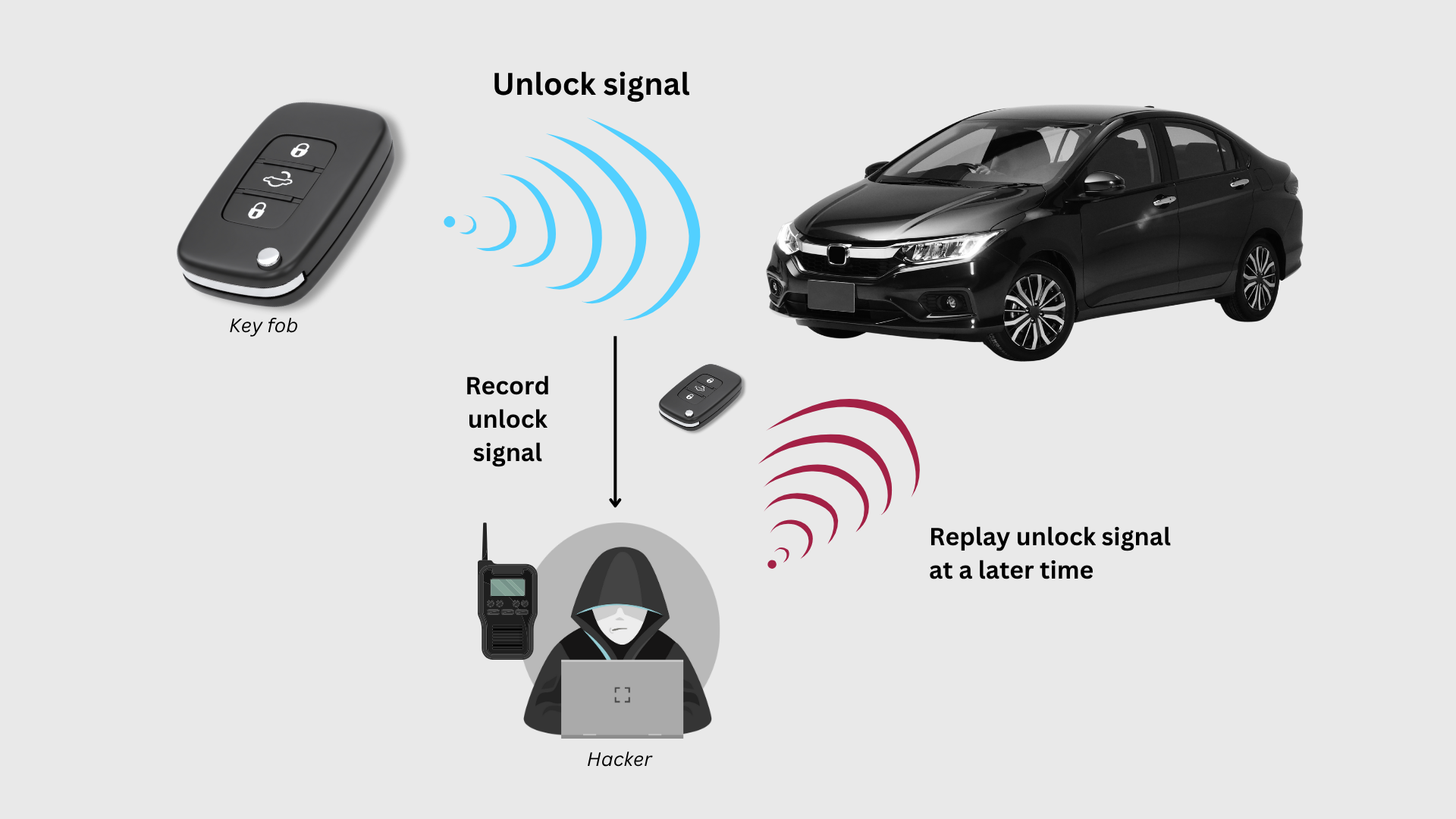
The Replay attack
Modern systems add rolling codes to stop simple replays. Each press sends a new code generated by a cryptographically secure PRNG, and the car checks the received code against an expected window before executing a command. This helps, but it has led to a new class of attack.
Roll-jam attack
Roll-jam attack targets the rolling-code scheme used by many key fobs. The attacker jams the channel so the car never receives the legitimate rolling code, while silently recording that code for later use. By blocking delivery and capturing the message, the attacker preserves a valid token that can be replayed at a time of their choosing.
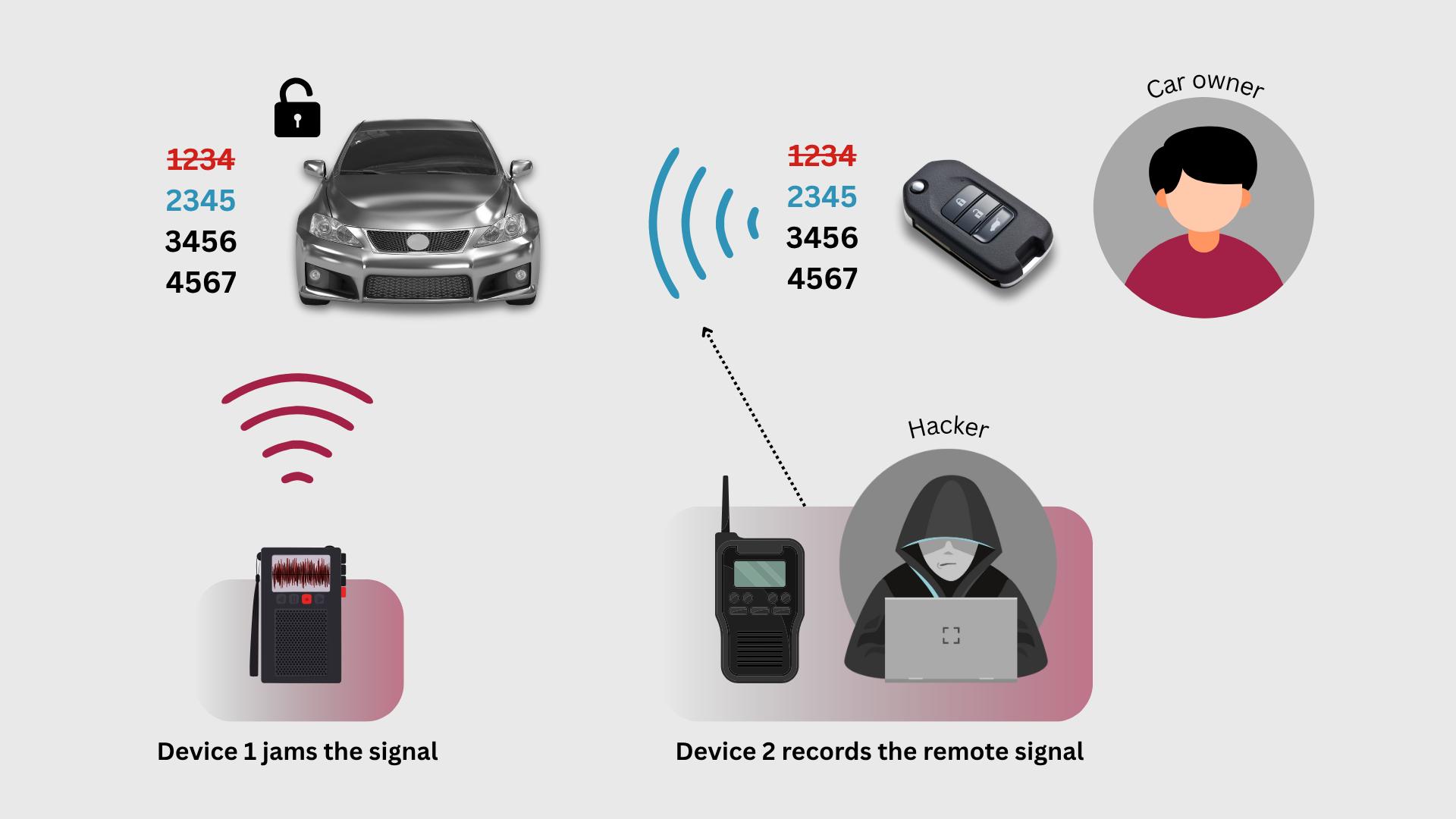
The Roll-jam attack
Once rolling codes are manipulated this way, anti-replay protections can fail in practice. A vehicle may be unlocked multiple times using forged messages, and if an algorithm or key leaks, entire product lines can be exposed. One real-world weakness is the use of independent code streams for Lock and Unlock. Separating the streams can stop naive reuse of a Lock code for Unlock, but it does not prevent an adversary from capturing the exact Unlock code they need and replaying it after jamming.
Mitigation requires more than code resynchronization. Messages should carry strong cryptographic authentication so that intercepted traffic cannot be turned into valid commands. In practice, this means adding a secure message authentication code such as AES-CMAC or HMAC, binding it to a secret key and to freshness data like nonces, sequence counters, and tight acceptance windows. Combined with careful link timing, anti-jamming detection, and coordinated LF–UHF proximity checks, these measures raise the bar against roll-jam in real deployments.
Relay attack
In a relay, the adversary does not break the protocol. The goal is to extend the effective communication range so the car “believes” the authorized device is nearby, which allows unlocking or even engine start while the fob is far away.
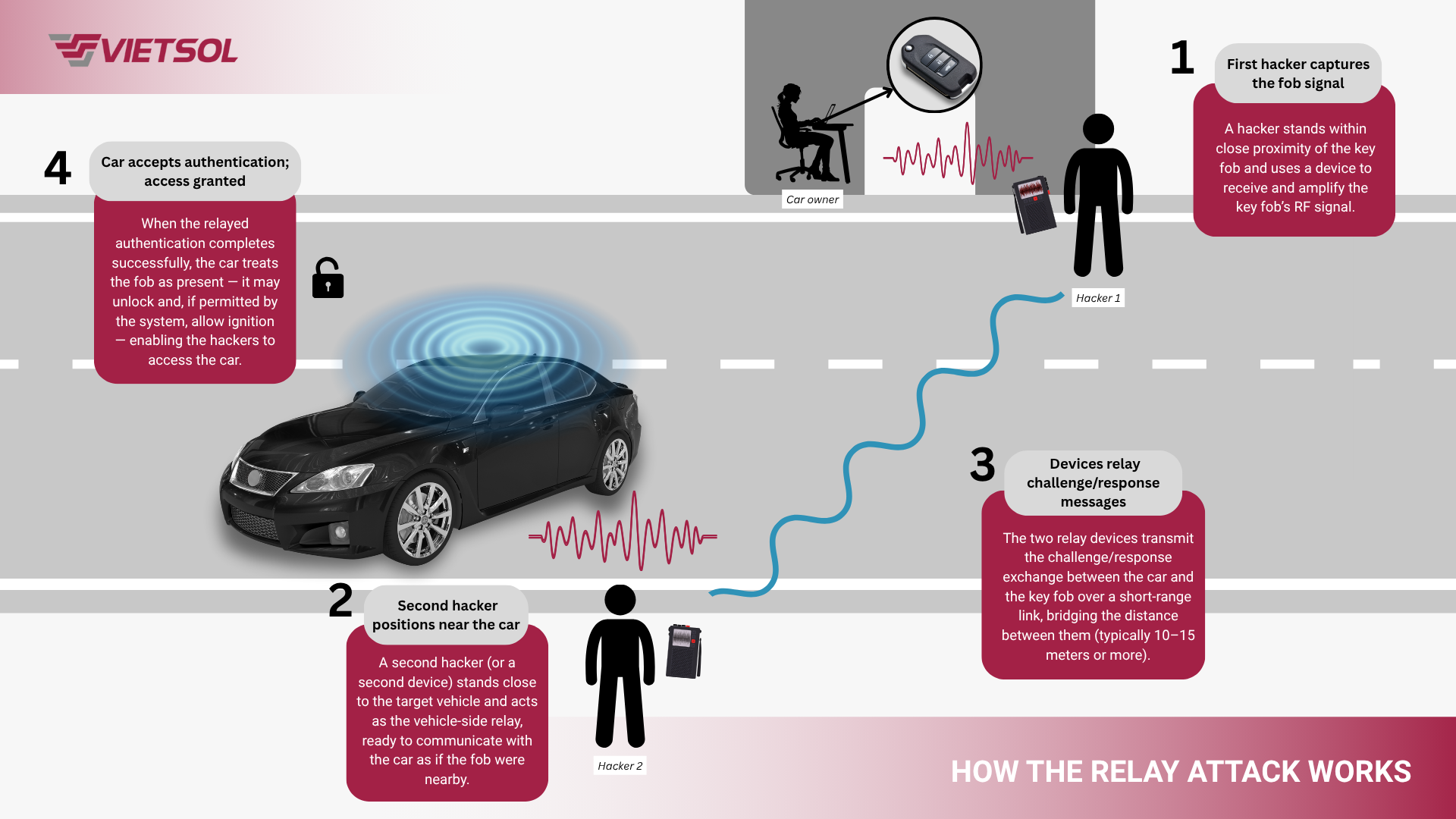
How the Relay attack works
In a typical setup, one attacker stands near the owner or the fob and captures the live signal, while an accomplice near the car relays that signal to the vehicle. Neither party needs to read or modify the content; they simply pass it along in real time to satisfy the proximity check.
The key difference from a replay attack is timing. Replay uses a previously recorded message at a later moment. Relay forwards an ongoing exchange as it happens, so neither endpoint needs to initiate contact with the other. In some cases, adversaries may amplify or slightly shape the signal, but the core idea is range extension rather than message forgery.
When key fob risks become real-world impact
Because the fob sits inside the authentication path, any flaw in transmission or verification can cascade into larger risks.
- From property to privacy: Attackers can unlock, start, or even steal a vehicle. Beyond property loss, breached systems can expose location, trip history, or personal data. Owners may be tracked or profiled without knowing it.
- Eroded trust and added costs: Fob-based attacks undermine confidence in vehicle safety. Users pay in repairs, rekeying, insurance claims, lost time, and degraded experience, which can influence future purchase decisions.
For automakers and component suppliers, any key fob incident can escalate into a reputational crisis. Once reports spread, trust erodes among customers and partners, with long-tail effects on sales, loyalty, and competitive position.
- Brand and reputation loss: A single key fob incident can snowball into a public relations crisis. As the story travels, customer and partner trust declines, with long-term consequences for revenue, loyalty, and competitive standing.
- Remediation costs and operational disruption: Because RF or key fob flaws are often exploited after products are in the field, recalls, re-evaluation, and large-scale fixes consume significant technical and financial resources. Costs can include end-to-end traceability, revalidation testing, firmware patch development and rollout, dealer support, insurance handling, and crisis communications. The magnitude of these efforts reinforces the value of building rigorous security testing into design and production from the very start.
- Legal and compliance exposure: As regulations and standards tighten, serious vulnerabilities can trigger liability and jeopardize certification under frameworks such as ISO/SAE 21434 and UNECE R155. Companies may face claims, penalties, and increased scrutiny from regulators.
Taken together, these realities argue for building key fob security from the start. Security testing is not an optional phase at the end of development. It is an essential practice that simulates credible attacks, measures system resilience, and surfaces weaknesses early so they can be fixed before exploitation. This reduces risk, protects brand equity, and strengthens consumer confidence.
Security testing is more than a technical requirement. It is a visible commitment to safety, reputation, and accountability in the era of connected vehicles.
Why security testing matters
Security testing is not a last-mile checklist at the end of development. It must run continuously to protect the vehicle at a system level. For RF-based key fob threats, rigorous testing answers a simple question: can the system truly block captured, replayed, or relayed signals under realistic conditions. By exercising those paths, latent weaknesses are verified in practice so manufacturers can harden designs proactively rather than react to incidents in the field.
To make the risk tangible, Vietsol has produced a controlled roll-jam demonstration showing how a captured rolling code can be used to unlock a vehicle. The goal is awareness backed by engineering evidence. Demonstrations like this validate attack feasibility, quantify exposure, and prove whether countermeasures work as intended.
Roll-jam attack on car key fob – Vietsol Demo
Vietsol’s programs follow ISO/SAE 21434 and UNECE R155 and incorporate TARA for structured threat analysis and risk assessment. Our engineers test early in development, covering the key fob path, the in-vehicle network, and wireless modules as parts of a single security story. This approach surfaces issues sooner, shortens mitigation cycles, and yields designs that are more resilient in real conditions.
Built on research and hands-on deployment, Vietsol is prepared to partner with automakers to develop comprehensive automotive cybersecurity strategies. In that strategy, security testing is not merely an evaluation step. It is integral to protection and safe operation across the vehicle’s lifecycle.
Conclusion
Key fob weaknesses are only one piece of the automotive cybersecurity puzzle. As vehicles depend more on wireless links such as RF, Bluetooth, Wi-Fi, and V2X, every channel becomes a potential pathway for systemwide risk. Security testing must therefore move beyond device-by-device checks. It should operate as a defense strategy that spans wireless communication layers, in-vehicle networks like CAN, LIN, and Ethernet, the ECUs that sit on those networks, and external interfaces.
In upcoming articles, Vietsol will continue to explore wireless communication in automotive cybersecurity, where smarter connectivity goes hand in hand with stricter safeguards to protect user safety and privacy.

 Tiếng Việt
Tiếng Việt
RELATED NEWS
When the Key Fob Becomes an Entry Point: The Role of Security Testing
Most drivers consider the smart key system one of the safest and most convenient features in modern cars. Within that system, the key fob is the handheld transmitter that acts as a digital key, allowing the vehicle to recognize its owner and grant access. The convenience feels effortless because it...
Vietsol and SEVASA Partner to Pioneer Smart EV Charging Solutions in Vietnam
On October 16, 2025, at Vietsol’s office in Hanoi, Vietsol Co., Ltd. and SEVASA Inc. (South Korea) officially signed a Letter of Intent (LOI) to cooperate in smart energy infrastructure and e-mobility. This collaboration aims to combine SEVASA’s innovative charging technologies with Vietsol’s local market expertise and implementation capabilities, paving...
From Euro NCAP Ratings to ASPICE Processes: Shaping DMS/OMS Development in Automotive
As the automotive industry enters the era of intelligent vehicles, expectations for in-vehicle safety assistance are higher than ever. Driver and Occupant Monitoring Systems (DMS/OMS) are now indispensable to active safety. To ensure maximum performance and reliability, DMS/OMS development should meet Euro NCAP requirements that define rating protocols and test...